Pre-emptive scheduling algorithms are more efficient than non-pre-emptive one. Discuss and compare FCFS and SJF algorithm from pre-emptive point of view.What is meant by Interprocess communication.
Write short notes on Directory implementation and Recovery.
Write short notes on Scrap-Space Management.
Describe the componnts of Operating System. What are the various services provided by the operating system towards users.Write important functions of Operating System.
Write notes on System Calls.
Write notes on Operating System Structure.
What is process?How process differs from program.Write process state diagram.What do you mean by thread ? Why threads is called light weight process?
What is Scheduler ? Compare short term,long term and medium term scheduler.
Write Barker's algorithm for avoiding deadlock with example.Write the characterstics of deadlock in details.
Write notes on Deadlock detection.
Write notes on Deadlock prevention.
Write notes on Recovery from deadlock.
Compare contiguous and non-contiguous memory allocation.
What do you mean by Pagefault ? How to handel Pagefault.Discuss brifely virtual memory management.
Explain any one of the secondary storage device.Write Sequential and Random file organization wit respect to advantages and disadvantages.
Write notes on File Protection Method.
Write notes on Disk Structure.
Write notes on Various File access Method.
What do you mean by Operating System. Write its characteristics and objectives.Compare multiprogramming and time sharing operating system.
Write short notes on System architecture.
Write short notes on Parallel system.
Write short notes on Distributed system.
Write short notes on Multiple processor scheduling.
Write short notes on Real time scheduling
Write short notes on Interprocess Communication
Write short notes on Process state diagram.
Compare logical and Physical address space. Define page and segmentation.Define demand paging and its implementation.
Explain page replacement algorithms.Explain briefly thrashing and demand segmentation.
Explain the working principle of hard disk.Explain the various directory structure in file system.
Write notes on Disk space management.
Write notes on Disk reliability.
Write notes on File protection.
Explain the structure layer of Operating System.Describe briefly components of Operating System.
What is process? How process is differ from program? Explain process state diagram.Explain multiple processor scheduling?
Write short notes on Thread.
Write short notes on Interprocess Communication.
Write the deadlock avoidance algorithm.What are the necessary condition of deadlock? How to detect deadlock?
Explain Peterson's solutions for more than one process.What do you mean by process synchronization? Explain briefly binary semaphore.
Compare contiguous and non-contiguous memory allocation wityh examples.
Describe the advantages of virtual memory and its implementations.
Write short notes on Swapping.
Write short notes on Thrasing.
Explain various allocations methods with respect to file.Describe briefly disk space management with respect to file.
Write the advantages and disadvantages of file organization (sequential file and index sequential file).Describe different types of directory structure w.r.t computer system.
Explain the purpose of system calls and discuss the system calls related to Process Control and File Manipulation.Discuss about various components of Operating System.
What are the services Operating System provides to its users?Write shortnotes on Batch Systems and Time- Sharing Systems.
What are various Inter-Process Communication Mechanisms provided by the Operating System for processes to communication with each other?
Write short notes on Multilevel Queue Scheduling.
Write short notes on cooperating processes.
What do you mean by Process? What are the different states of a Process? Explain with diagram.
What is a Critical Section Problem? Give the conditions that a solution to the critical section problem must satisfy. What is Bounded Buffer Problem? Give a solution to the bounded-buffer problem using semaphore.
What are the necessary conditions of deadlock? How can we prevent the occurence of a deadlock? How can we detect the occurence of a deadlock in a system with seversl instances of a Resource Type? How can we recover from a deadlock?>
Discuss the procedure for handling the page fault in demand paging.Consider the reference string:7,0,1,2,0,3,0,4,2,3,0,3,2,1,2,0,1,7,0,1 for a memory with three frames. Calculate the number of page faults with FIFO and Optimal page replacement algorithms.
Explain the concept of segmentation in detail with diagrams.What is thrashing? What is the cause of thrashing? How does the system detect thrashing? What can the system do to eliminate this problem?
Explain various file access methods in detail.What are various directory structures used by the Operating System to manage files in the file system?
Write short notes on SJF DiskScheduling scheme.
Write short notes on FCFS DiskScheduling scheme
Write short notes on SSTF Disk Scheduling scheme.
Explain the three allocation methods in file system implementation. Illustrate with proper diagram.
Describe the differences between symmetric and asymmetric multiprocessing.What are the advantages and disadvantages of multiprocessor systems?
Define the essential properties of the fllowing types of operating systems Batch,Time sharing,Real Time.
List five services provided by an operating system.Explain how each provides convenience to the user. Explain also in which case it would be impossible for user-level programhs to provide tehse services.
When are caches useful?What problems do they solve?what problem do they cause ?If a cache can be made as large as the device for which it is caching,why not make it that large and eliminate the device?
Describe the difference among short-term,medium-term,and long term scheduling.
Define the difference between preemptive and nonpreemptive scheduling.State why strict non-preemptive scheduling
unlikely to be used in a computer center.
What is the meaning of the term busy waiting?What other kinds of waiting are there in an O.S.?Can busy waiting be avoided altogrther?Explain your answer.Show that, if the wait signal operations are not executed automatically then mutual exclusion may be violated.
Suppose that an system is in a unsafe state.Show that it is possible for the processes to complete their excution without entering a deadlock state.
Conisder a system consisting of 'm' resources of the same type ,being shared by 'n' processes.Resources can be requested and released by processes only one at a time.
Show the system is deadlock free if the following two conditions hold The maximum need of each process is between 1 and 'm' resouces.The sum of all maximum needs is less than m+n.
Why are pages sizes always powers of2.Explain the following allocation algorithms First-fit,Best-fit and Worst-fit.
When do page fault occur?Describe the action taken by the Operating System when a page fault occurs.
Explain the difference between logical and physical address.Explain the difference between internal and external fragmentation.
Give an example on an application in which data in a file should be accessed in the following order Sequentially and Randomly.
Explain the purpose of the open and close operations.
Why must the bit map for file allocation be kept on mass storage,rather than in main memory?In what situation would using memory as a RAM disk be more useful than using it as a disk cache?
What is an Operating System? Illustrate evolution and structure of different Operating System. What are the different characteristics of Modern Operating System?How do you implement an Operating System?
An operating system (OS) is the program that, after being initially loaded into the computer by a boot program, manages all of the other application programs in a computer. The application programs make use of the operating system by making requests for services through a defined application program interface (API).
The communication between a user and a system takes place with the help of an operating systems. Windows, Linux, and Android are examples of operating systems that enable the user to use programs like MS Office, Notepad, and games on the computer or mobile phone.
What is an Operating System? Discuss the differences between Batch, time sharing and Real-time operating system.What are the main purpose of an operating system? Discuss in brief.
An operating system (OS) is the program that, after being initially loaded into the computer by a boot program, manages all of the other application programs in a computer. The application programs make use of the operating system by making requests for services through a defined application program interface (API).
What system call? Write different types of system call.What are the various services provided by Operating System?
In computing, a system call is the programmatic way in which a computer program requests a service from the kernel of the operating system on which it is executed. This may include hardware-related services (for example, accessing a hard disk drive or accessing the device's camera), creation and execution of new processes, and communication with integral kernel services such as process scheduling. System calls provide an essential interface between a process and the operating system.
Write notes on Virtual Machine.
In computing, a virtual machine (VM) is the virtualization/emulation of a computer system. Virtual machines are based on computer architectures and provide functionality of a physical computer. Their implementations may involve specialized hardware, software, or a combination. Therefore virtual machine creates a virtual environment that works like a computer within a computer. It runs on an isolated partition of its host computer with its own CPU power, memory, operating system (such as Windows, Linux, macOS), and other resources. End users can run applications on VMs and use them as they normally would on their workstation.
Virtual machines are made possible through virtualization technology. Virtualization uses software to simulate virtual hardware that allows multiple VMs to run on a single machine. The physical machine is known as the host while the VMs running on it are called guests.
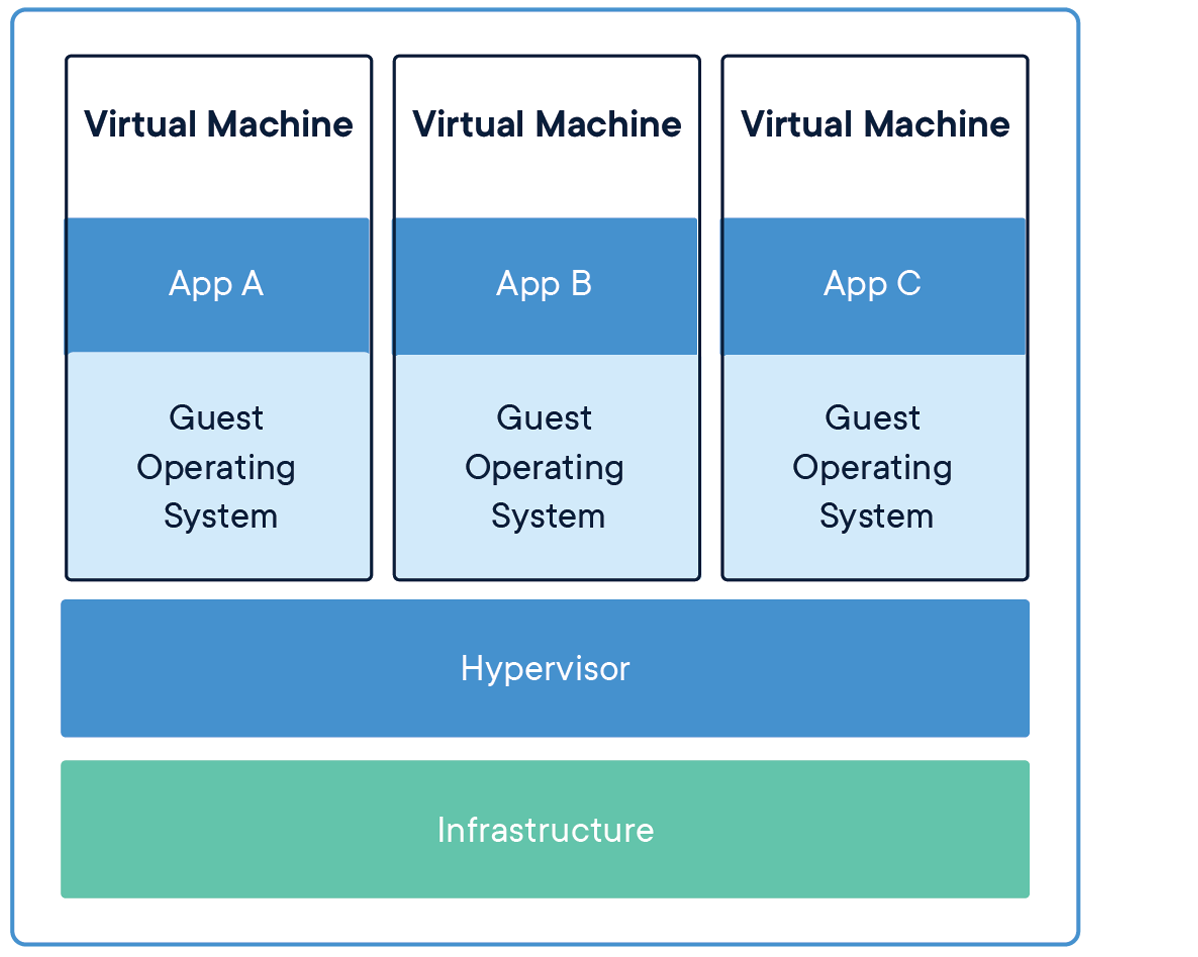
VMs are isolated from the rest of the system, and multiple VMs can exist on a single piece of hardware, like a server. They can be moved between host servers depending on demand or to use resources more efficiently.
VMs allow multiple different operating systems to run simultaneously on a single computer—like a Linux distro on a MacOS laptop. Each operating system runs in the same way an operating system or application normally would on the host hardware, so the end user experience emulated within the VM is nearly identical to a real-time operating system experience running on a physical machine.
Write short notes on Real time operating system.
A real-time operating system (RTOS) is a special-purpose operating system used in computers that has strict time constraints for any job to be performed. It is employed mostly in those systems in which the results of the computations are used to influence a process while it is executing. Whenever an event external to the computer occurs, it is communicated to the computer with the help of some sensor used to monitor the event. The sensor produces the signal that is interpreted by the operating system as an interrupt. On receiving an interrupt, the operating system invokes a specific process or a set of processes to serve the interrupt.
This process is completely uninterrupted unless a higher priority interrupt occurs during its execution. Therefore, there must be a strict hierarchy of priority among the interrupts. The interrupt with the highest priority must be allowed to initiate the process , while lower priority interrupts should be kept in a buffer that will be handled later. Interrupt management is important in such an operating system. Real-time operating systems employ special-purpose operating systems because conventional operating systems do not provide such performance.
What do you mean by process scheduling? Discuss various activities performed in process scheduling. State and explain performance measures of process scheduling algorithms.
The process scheduling is the activity of the process manager that handles the removal of the running process from the CPU and the selection of another process on the basis of a particular strategy.
Process scheduling is an essential part of a Multiprogramming operating systems. Such operating systems allow more than one process to be loaded into the executable memory at a time and the loaded process shares the CPU using time multiplexing.
Write short notes on Inter Process Communication.
Inter Process Communication is the mechanism provided by the operating system that allows processes to communicate with each other. This communication could involve a process letting another process know that some event has occurred or the transferring of data from one process to another.
Inter Process Communication allows the exchange of data between processes. It enables resource and data sharing between the processes without interference.
IPC Models
There are two fundamental models of IPC which are as follows −
Shared memory
A region of memory that is shared by cooperating processes is established. Processes can then exchange information by reading and writing data to the shared region.
Message passing
Communication takes place by means of messages exchanged between the cooperating processes. Message passing is useful for exchanging small amounts of data because no conflicts need be avoided.
Write short notes on Mutual Exclusion.
Mutual exclusion is a property of process synchronization which states that “no two processes can exist in the critical section at any given point of time”. Mutual exclusion prevents simultaneous access to a shared resource. The shared resource is a data object, which two or more concurrent threads are trying to modify. Mutual exclusion algorithm ensures that if a process is already performing write operation on a data object [critical section] no other process/thread is allowed to access/modify the same object until the first process has finished writing upon the data object [critical section] and released the object for other processes to read and write upon.
Write short notes on Critical Region.
Sometimes a process has to access shared memory or files, or do other critical things that can lead to races. That part of the program where the shared memory is accessed is called the critical region or critical section.
If we could arrange matters such that no two processes were ever in their critical regions at the same time, we could avoid races. Although this requirement avoids race conditions, it is not sufficient for having parallel processes cooperate correctly and efficiently using shared data.
We need four conditions to hold to have a good solution:
1) No two processes may be simultaneously inside their critical regions.
2) No assumptions may be made about speeds or the number of CPUs.
3) No process running outside its critical region may block other processes.
4) No process should have to wait forever to enter its critical region.
Write short notes on Synchronization.
Processes Synchronization or Synchronization is the way by which processes that share the same memory space are managed in an operating system. It helps maintain the consistency of data by using variables or hardware so that only one process can make changes to the shared memory at a time. There are various solutions for implementing Synchronization, such as semaphores, Mutual Exclusion locks, synchronization hardware etc.
What do you mean by semaphores? How the P and V semaphores are used to ensure mutual exclusion?What are the different steps taken to recover from deadlock situation?
In a Computer System, we have a limited amount of resources that are being shared between various processes. One resource should be used by only one process at a time. This is called process synchronization. So, in an Operating System, we must have synchronization between various processes. This synchronization between processes can be achieved with the help of semaphore.
A semaphore is a synchronization object that controls access by multiple processes to a common resource in a parallel programming environment. Semaphores are widely used to control access to files and shared memory. The three basic functionalities associated with semaphores are set, check and wait until it clears to set it again.
What are the types of Semaphore? Explain binary senaphore.
Semaphore are of two types, binary semaphore and counting semaphore.
A binary semaphore is restricted to values of zero or one. A binary semaphore can be used to control access to a single resource. In particular, it can be used to enforce mutual exclusion for a critical section in user code.
A counting semaphore can assume any nonnegative integer value. A counting semaphore can be used to control access to a pool of two or more resources.
Write short notes on Paging.
Paging is a function of memory management where a computer will store and retrieve data from a device’s secondary storage to the primary storage. Memory management is a crucial aspect of any computing device, and paging specifically is important to the implementation of virtual memory.
Paging works by writing data to, and reading it from, secondary storage for use in primary storage. Paging is a basic function in memory management for a computer's operating system (OS) as well -- this includes Windows, Unix, Linux and macOSs.
In a memory management system that takes advantage of paging, the OS reads data from secondary storage in blocks called pages, all of which have identical size. The physical region of memory containing a single page is called a frame. When paging is used, a frame does not have to comprise a single physically contiguous region in secondary storage. This approach offers an advantage over earlier memory management methods, because it facilitates more efficient and faster use of storage.
What do you mean by Demand paging? What is page fault? How the page fault frequency depends on the page size?
Demand paging is a technique used in virtual memory systems where the pages are brought in the main memory only when required or demanded by the CPU. Hence, it is also named as lazy swapper because the swapping of pages is done only when required by the CPU.
Advantages of Demand paging
It increases the degree of multiprogramming as many processes can be present in the main memory at the same time.
There is a more efficient use of memory as processes having size more than the size of the main memory can also be executed using this mechanism because we are not loading the whole page at a time.
Disadvantages of Demand paging
The amount of processor overhead and the number of tables used for handling the page faults is greater than in simple page management techniques.
Write short notes on Segmentation.
Segmentation:
In Operating Systems, Segmentation is a memory management technique in which the memory is divided into the variable size parts. Each part is known as a segment which can be allocated to a process. The details about each segment are stored in a table called a segment table. Segment table is stored in one (or many) of the segments.
Segment table contains mainly two information about segment:
1) Base: It is the base address of the segment
2) Limit: It is the length of the segment.
Advantages of Segmentation
No internal fragmentation
Average Segment Size is larger than the actual page size.
Less overhead
It is easier to relocate segments than entire address space.
The segment table is of lesser size as compared to the page table in paging.
Disadvantages
It can have external fragmentation.
it is difficult to allocate contiguous memory to variable sized partition.
Costly memory management algorithms.
Write short notes on File allocation methods.
The allocation methods define how the files are stored in the disk blocks. There are three main disk space or file allocation methods.
1) Contiguous Allocation
2) Linked Allocation
3) Indexed Allocation
The main idea behind these methods is to provide:
1) Efficient disk space utilization.
2) Fast access to the file blocks.
1. Contiguous Allocation
In this scheme, each file occupies a contiguous set of blocks on the disk. For example, if a file requires n blocks and is given a block b as the starting location, then the blocks assigned to the file will be: b, b+1, b+2,……b+n-1. This means that given the starting block address and the length of the file (in terms of blocks required), we can determine the blocks occupied by the file.
The directory entry for a file with contiguous allocation contains
Address of starting block
Length of the allocated portion.
2. Linked Allocation
In this scheme, each file is a linked list of disk blocks which need not be contiguous. The disk blocks can be scattered anywhere on the disk.
The directory entry contains a pointer to the starting and the ending file block. Each block contains a pointer to the next block occupied by the file.
3. Indexed Allocation
In this scheme, a special block known as the Index block contains the pointers to all the blocks occupied by a file. Each file has its own index block.
Write notes on File access method.
File Access Methods in Operating System
There are three ways to access a file into a computer system: Sequential-Access, Direct Access, Index sequential Method.
Sequential Access –
It is the simplest access method. Information in the file is processed in order, one record after the other. This mode of access is by far the most common; for example, editor and compiler usually access the file in this fashion.
Read and write make up the bulk of the operation on a file. A read operation -read next- read the next position of the file and automatically advance a file pointer, which keeps track I/O location. Similarly, for the -write next- append to the end of the file and advance to the newly written material.
Key points:
Data is accessed one record right after another record in an order.
When we use read command, it move ahead pointer by one
When we use write command, it will allocate memory and move the pointer to the end of the file
Such a method is reasonable for tape.
Direct Access –
Another method is direct access method also known as relative access method. A filed-length logical record that allows the program to read and write record rapidly. in no particular order. The direct access is based on the disk model of a file since disk allows random access to any file block. For direct access, the file is viewed as a numbered sequence of block or record. There is no restriction on the order of reading and writing for a direct access file.
A block number provided by the user to the operating system is normally a relative block number, the first relative block of the file is 0 and then 1 and so on.
Index sequential method –
It is the other method of accessing a file that is built on the top of the sequential access method. These methods construct an index for the file. The index, like an index in the back of a book, contains the pointer to the various blocks. To find a record in the file, we first search the index, and then by the help of pointer we access the file directly.
Key points:
It is built on top of Sequential access.
It control the pointer by using index.
What is disk scheduling? Describe different disk scheduling algorithms with examples.
Disk scheduling is done by operating systems to schedule I/O requests arriving for the disk. Disk scheduling is also known as I/O scheduling.
Disk scheduling is important because:
Multiple I/O requests may arrive by different processes and only one I/O request can be served at a time by the disk controller. Thus other I/O requests need to wait in the waiting queue and need to be scheduled.
Two or more request may be far from each other so can result in greater disk arm movement.
Hard drives are one of the slowest parts of the computer system and thus need to be accessed in an efficient manner.
Disk Scheduling Algorithms
1) FCFS scheduling algorithm
2) SSTF (shortest seek time first) algorithm
3) SCAN scheduling
4) C-SCAN scheduling
5) LOOK Scheduling
6) C-LOOK scheduling
FCFS: FCFS is the simplest of all the Disk Scheduling Algorithms. In FCFS, the requests are addressed in the order they arrive in the disk queue.
Advantages:
Every request gets a fair chance
No indefinite postponement
Disadvantages:
Does not try to optimize seek time
May not provide the best possible service
SSTF: In SSTF (Shortest Seek Time First), requests having shortest seek time are executed first. So, the seek time of every request is calculated in advance in the queue and then they are scheduled according to their calculated seek time. As a result, the request near the disk arm will get executed first. SSTF is an improvement over FCFS as it decreases the average response time and increases the throughput of system.
Advantages:
Average Response Time decreases
Throughput increases
Disadvantages:
Overhead to calculate seek time in advance
Can cause Starvation for a request if it has higher seek time as compared to incoming requests
High variance of response time as SSTF favours only some requests
SCAN: In SCAN algorithm the disk arm moves into a particular direction and services the requests coming in its path and after reaching the end of disk, it reverses its direction and again services the request arriving in its path. So, this algorithm works as an elevator and hence also known as elevator algorithm. As a result, the requests at the midrange are serviced more and those arriving behind the disk arm will have to wait.
Advantages:
High throughput
Low variance of response time
Average response time
Disadvantages:
Long waiting time for requests for locations just visited by disk arm
CSCAN: In CSCAN algorithm in which the disk arm instead of reversing its direction goes to the other end of the disk and starts servicing the requests from there. So, the disk arm moves in a circular fashion and this algorithm is also similar to SCAN algorithm and hence it is known as C-SCAN (Circular SCAN).
Advantages:
Provides more uniform wait time compared to SCAN
LOOK: It is similar to the SCAN disk scheduling algorithm except for the difference that the disk arm in spite of going to the end of the disk goes only to the last request to be serviced in front of the head and then reverses its direction from there only. Thus it prevents the extra delay which occurred due to unnecessary traversal to the end of the disk.
CLOOK: As LOOK is similar to SCAN algorithm, in similar way, CLOOK is similar to CSCAN disk scheduling algorithm. In CLOOK, the disk arm in spite of going to the end goes only to the last request to be serviced in front of the head and then from there goes to the other end’s last request. Thus, it also prevents the extra delay which occurred due to unnecessary traversal to the end of the disk.
Write notes on Directory Structure.
A directory is a container that is used to contain folders and files. In computing, a directory structure is the way an operating system arranges files that are accessible to the user. Files are typically displayed in a hierarchical tree structure.

Advantages of maintaining directory structure are
Efficiency: A file can be located more quickly.
Naming: It becomes convenient for users- for example two users can have same name for different files or may have different name for same file.
Grouping: Logical grouping of files can be done by properties e.g. all java programs, all games etc.
There are several logical structures of a directory, these are:
Single-Level Directory:
The single-level directory is the simplest directory structure. In it, all files are contained in the same directory which makes it easy to support and understand.
A single level directory has a significant limitation, when the number of files increases or when the system has more than one user. Since all the files are in the same directory, they must have a unique name.

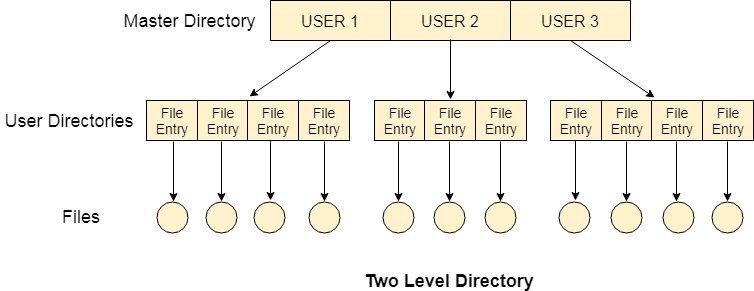
Two Level Directory:
In two level directory systems, we can create a separate directory for each user. There is one master directory which contains separate directories dedicated to each user. For each user, there is a different directory present at the second level, containing group of user's file. The system doesn't let a user to enter in the other user's directory without permission.
Tree Structured Directory:
In Tree structured directory system, any directory entry can either be a file or sub directory. Tree structured directory system overcomes the drawbacks of two level directory system. The similar kind of files can now be grouped in one directory.
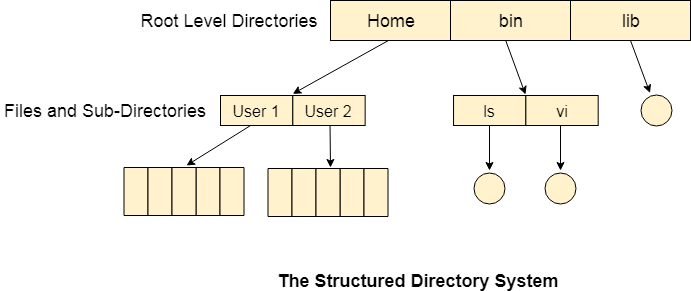
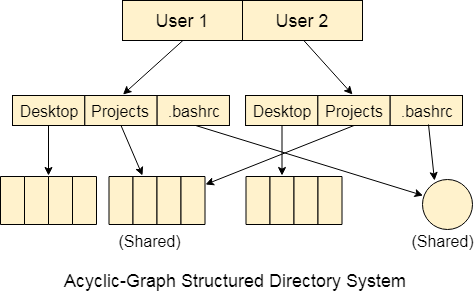
Acyclic-Graph Structured Directories:
The tree structured directory system doesn't allow the same file to exist in multiple directories therefore sharing is major concern in tree structured directory system. We can provide sharing by making the directory an acyclic graph. In this system, two or more directory entry can point to the same file or sub directory. That file or sub directory is shared between the two directory entries.